
Sarcoma Group Ransomware: A New Player in the Cyber-crime Ecosystem
The threat landscape in cybersecurity is constantly shifting, and among the emerging actors making waves is the Sarcoma Group, a relatively new ransomware gang that has begun to draw attention for its stealthy operations and high-impact attacks. While not yet as notorious as groups like LockBit or BlackCat, Sarcoma is exhibiting characteristics of a well-organized and dangerous cybercriminal operation.
Who Is the Sarcoma Group?
First observed in early 2024, Sarcoma Group operates under a Ransomware-as-a-Service (RaaS) model. This means the core developers create and maintain the ransomware infrastructure, while recruited affiliates execute attacks on selected targets. In return, affiliates share a cut of the ransom with the core group.
Sarcoma appears to favor targeted attacks over mass infections, often aiming at mid-to-large enterprises across various sectors, including manufacturing, logistics, and public services.

Attack Strategy: Double Extortion
Sarcoma Group follows the modern double extortion playbook, which includes:
Encrypting data on compromised systems to disrupt business operations.
Exfiltrating sensitive data and threatening to publish it on a Tor-based leak site if ransom demands are not met.
This method is designed to increase leverage during ransom negotiations, as organizations face both operational downtime and the risk of public data leaks.
Technical Characteristics
Though analysis is ongoing, samples attributed to Sarcoma ransomware demonstrate several advanced features:
AES/RSA hybrid encryption for speed and strength.
Use of LOLBins (Living Off the Land Binaries) to evade detection.
Disabling shadow copies and backups to prevent recovery without payment.
Credential harvesting and lateral movement using tools like Mimikatz and Cobalt Strike.
Obfuscation techniques that make detection by traditional antivirus solutions more difficult.
Initial access is often gained through phishing campaigns, RDP brute-force, or exploitation of unpatched vulnerabilities in public-facing systems.
Leak Site and Public Disclosures
Sarcoma Group maintains a .onion leak site on the dark web, where they post details and sample data from non-paying victims. The site is professionally structured, with sections for upcoming leaks, “proof” files, and timelines for when data will be published if no payment is received.
While we can’t display images from the dark web directly, threat intelligence analysts report that the Sarcoma leak site mimics the style of other major ransomware groups—employing branding, countdown timers, and searchable victim data.
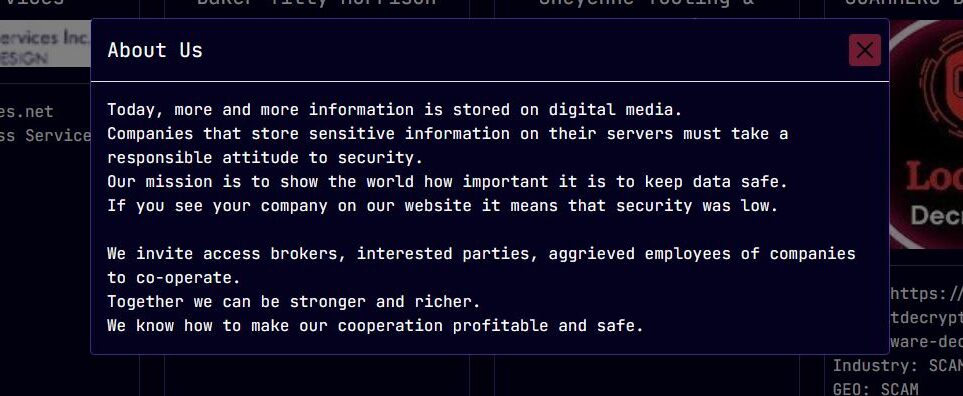
Notable Incidents
Although still emerging, Sarcoma has already claimed several victims, including:
A European logistics company with operations disrupted for days
A U.S.-based construction firm whose internal documents were leaked online
A healthcare services provider forced to shut down certain systems
In these cases, ransom demands ranged from $250,000 to $3 million, depending on the size of the organization and the volume of data exfiltrated.
Defense and Mitigation
To protect against Sarcoma and similar threats, organizations should take the following precautions:
Regularly patch systems and apply security updates.
Use multi-factor authentication (MFA) on all remote access points.
Implement network segmentation to limit lateral movement.
Deploy EDR solutions with real-time threat detection capabilities.
Backup data regularly, and store backups offline or in immutable storage.
Educate employees on phishing and social engineering tactics.
Final Thoughts
The Sarcoma Group may be new to the ransomware arena, but their tactics and infrastructure suggest they are not amateurs. As their operations expand and affiliate network grows, businesses should remain alert and strengthen their cyber defenses.
Cybersecurity is no longer optional—it’s foundational. Early detection, response readiness, and a zero-trust mindset can help mitigate the risk posed by groups like Sarcoma and other evolving ransomware threats.
